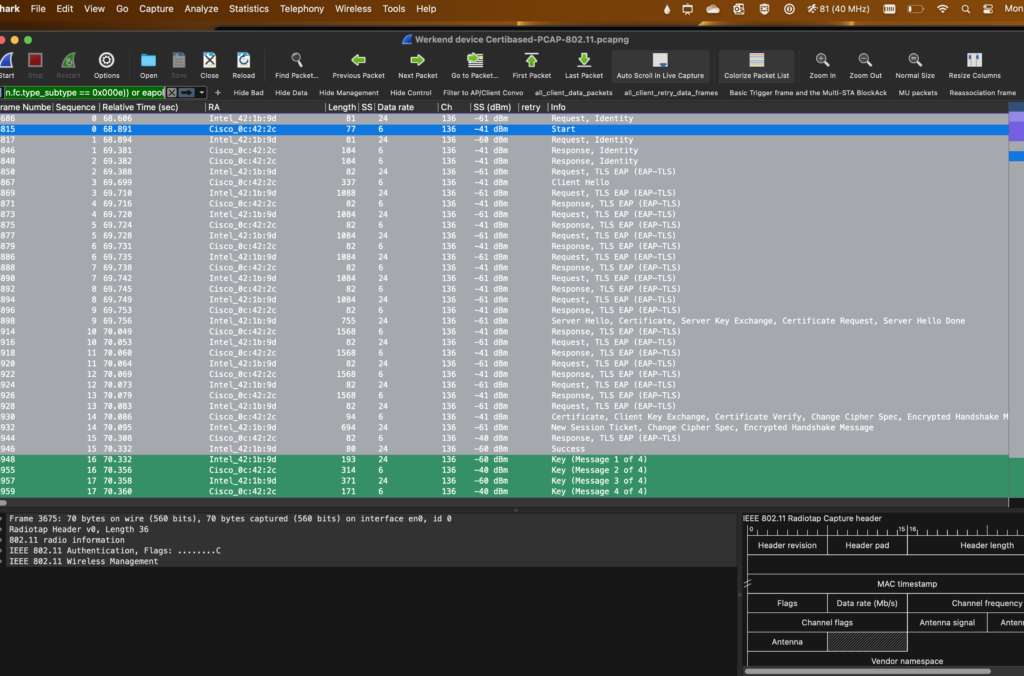
EAP-TLS (Extensible Authentication Protocol with Transport Layer Security) provides a secure way for devices to authenticate themselves on a wireless network.
The EAP-TLS authentication process involves the exchange of frames between the client (the device trying to connect to the network) and the authentication server.
There is a Client Hello (EAP-TLS Response): The client responds with a Client Hello frame, initiating the TLS handshake.
This frame contains information about the cryptographic capabilities of the client and initiates the negotiation of security parameters.
And there is a Server Hello (EAP-TLS Start): In response to the EAPOL-Start frame, the AP sends an EAP-TLS Start frame.
This frame includes information necessary for initiating the TLS handshake, such as the supported cryptographic algorithms.
Both the client and the authentication server exchange digital certificates to establish the authenticity of each other.
The client presents its certificate to the server, and the server presents its certificate to the client.
Finish (EAP-Success or EAP-Failure): Based on the outcome of the TLS handshake, the authentication server sends an EAP-Success frame if the authentication is successful, or an EAP-Failure frame if the authentication fails. This EAP-TLS frame exchange ensures a secure and authenticated connection between the client and the wireless network, providing a robust foundation for data protection and privacy in wireless communications.
I used a name resolution filter for better reading.
The Pcap was also taken using my MacBook PRO m2, together with Adrian Granados AIRTOOL (great tool!)
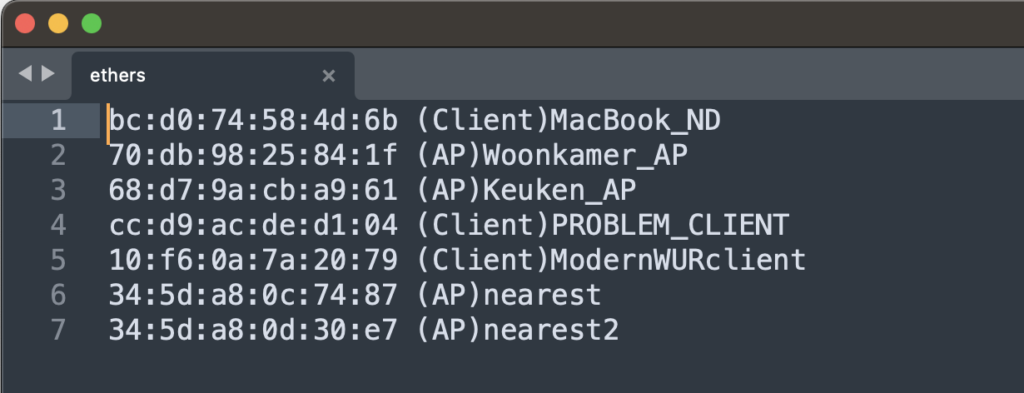
To get the name resolution in your pcap on your Mac go to the Wireshark directory ~/.config/wireshark , open the ethers file in your favorite editor (Sublime for me).
In Wireshark I added a filter so I see only the necessary authentication frames between the client STA and the AP.
Hide control frames and add client / AP conversation:
!wlan.fc.type == 1 and wlan.ta == 34:5d:a8:0c:74:87 and wlan.ra == 10:f6:0a:7a:20:79 or wlan.ra == 34:5d:a8:0c:74:87 and wlan.ta == 10:f6:0a:7a:20:79
Some observations:
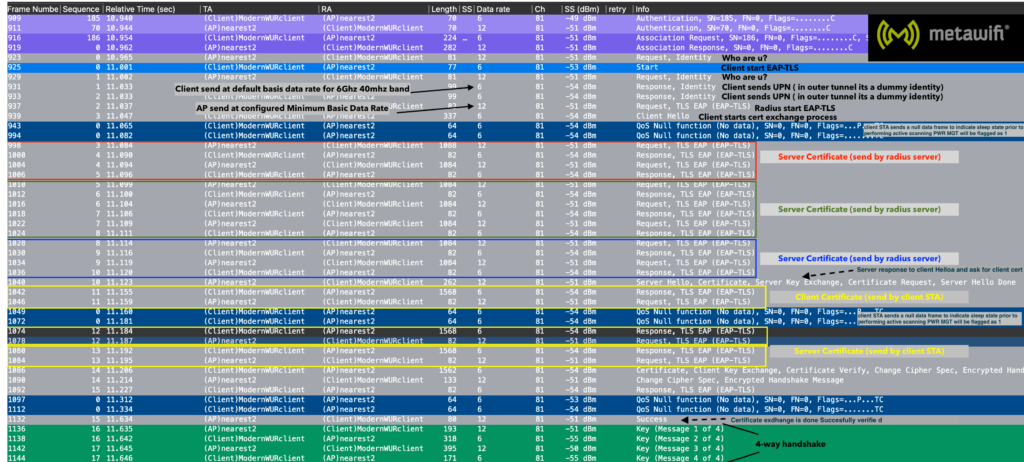
Note that the Mandatory data rate is set to 12Mbit in this environment, the client sends these frames at its lowest speed 6Mbit. Data rate speed will follow the Mandatory rate set on the WLC or AP. The entire authentication process is completed within 634 milliseconds, not so fast… but that’s why we need 802.11r implemented. After the initial handshake, this can be reduced to under 50 ms.
Also not that the client sends these frames on the lowest data rate possible 6Mbit. The Access-Points replies with a data rate of 12Mbit because it is set to do that. After the 4-way handshake, everything is encrypted and the data frames are transmitted on 12mbit by the client.
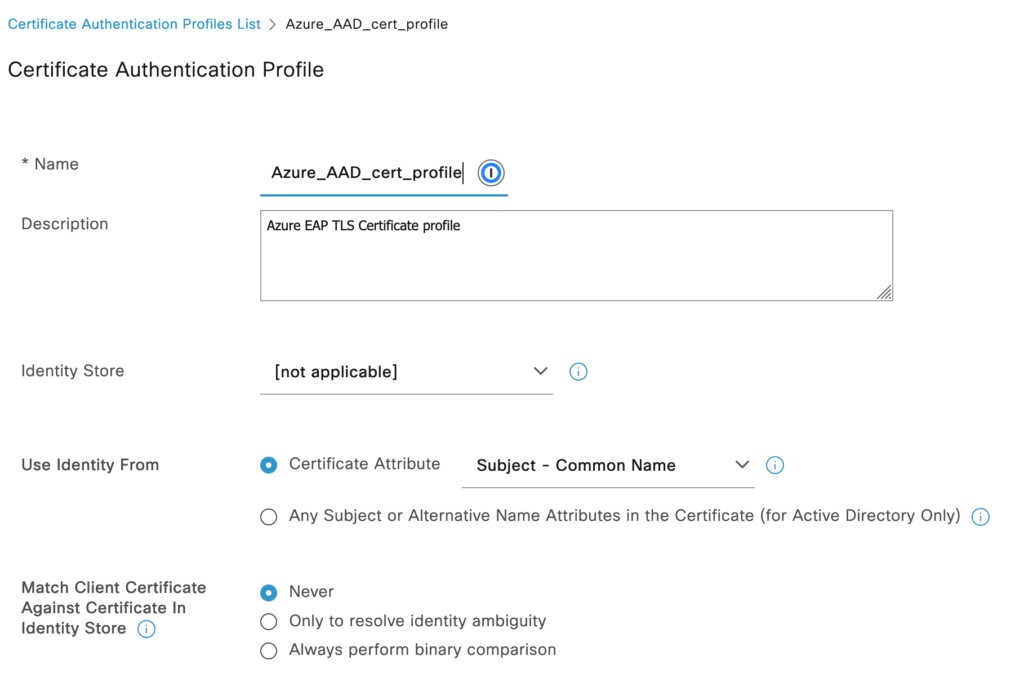
In Cisco ISE I added a Certificate template that looks at the Common Name of the client certificate.
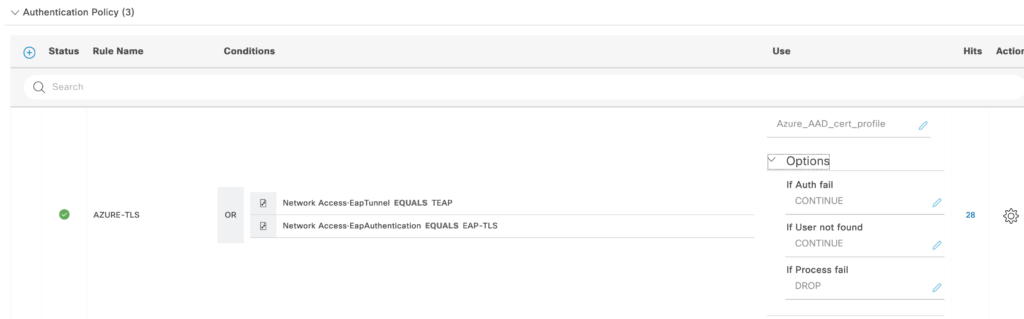
This is added as the Authentication Policy
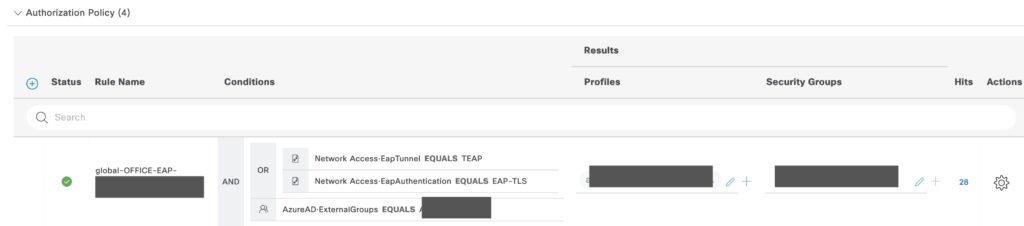
In the authorization Policy, you can add any AD or AAD group (If you have the connection done (works from ISE 3.2+)
Note – update 1-04-2024
Since Windows 11, the OS does not allow PEAP mschapv2 authentication anymore on machine-based authentication. This will impact a lot of enterprises as they are forced to generate a certificate for each domain joined STA. The authentication flow is similar