WPA3 OWE (Opportunistic Wireless Encryption) in transition mode requires creating a hidden (non-broadcasted) SSID. When I was reading about this I was thinking: “we fight for years to get rid of Hidden SSID” and now we must create one again to get this solution to work for older clients. Let’s see how it works.
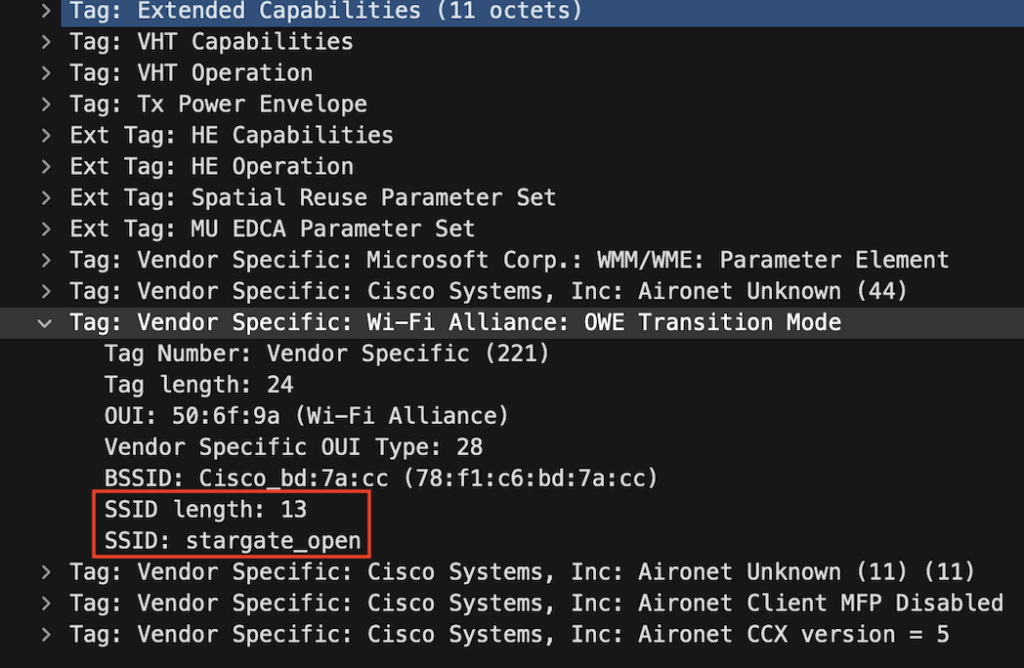
A non-hidden SSID was created that is broadcasted SSID ’stargate_open’. the Beacon has a Wi-Fi Alliance: OWE Transition Mode element in it, that will contain the SSID “stargateOWE” when the client is WPA3 OWE capable it will redirect the client like magic to the SSID “stargateOWE”.
Note: There is no RSN (Robust Security Network) element, is because it’s open.
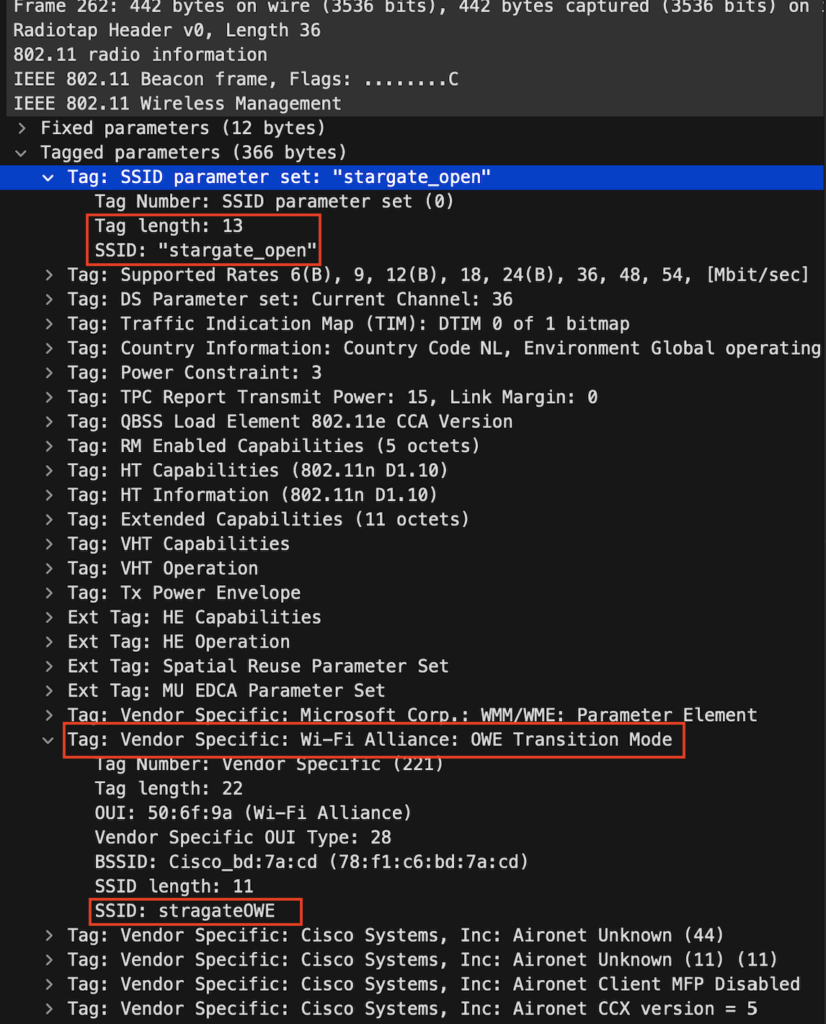
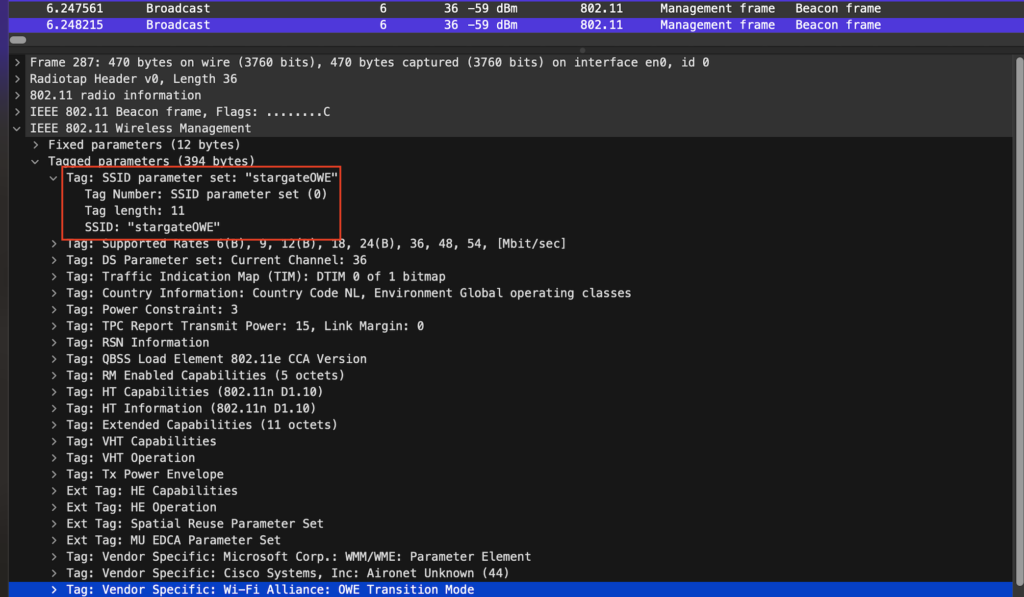
In the captured beacon frame below we can see the SSID ’stargateOWE’ is not broadcasted because the length is 0. This beacon has the actual RSN security element because it’s enhanced open.
In the RSN , capabilities we can see this time it’s there, and the Management Frame Protection (MFP) is flagged to true (1)
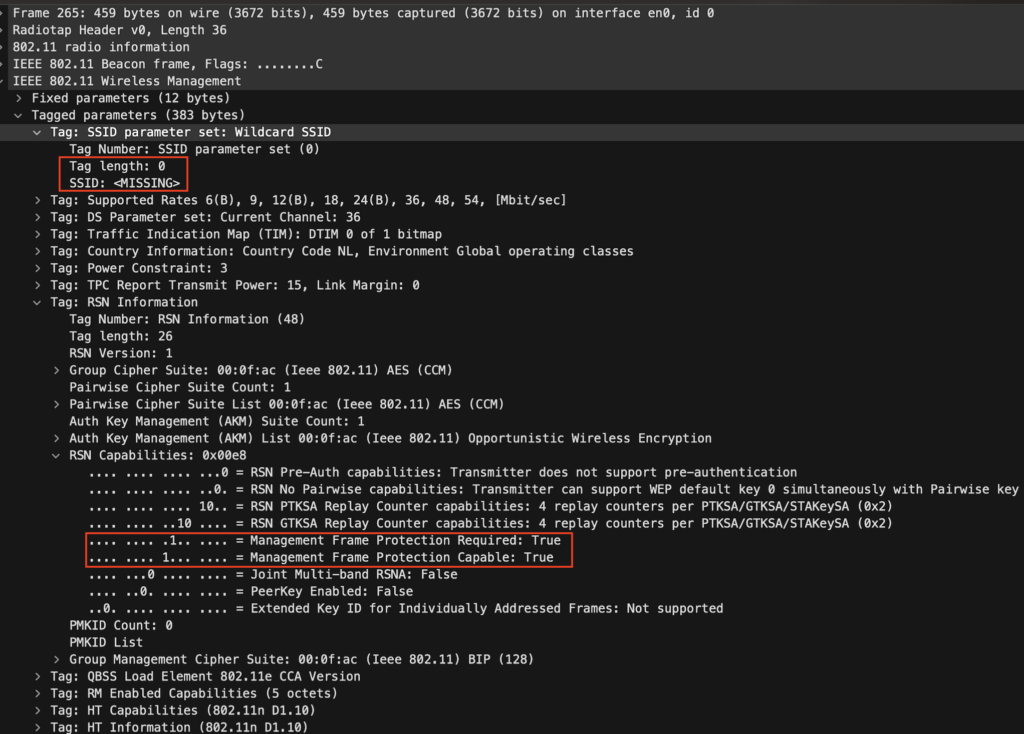
The Wi-Fi Alliance: OWE Transition Mode element is there again, pointing to the stargate_open, in this case, it only allows transition when coming from stargate_open.
When the client doesn’t support OWE it will connect to the SSID stargate_open

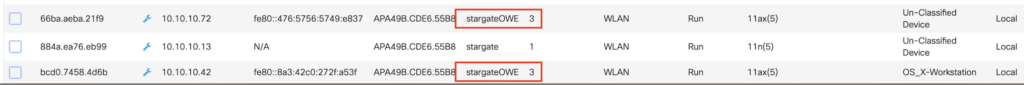
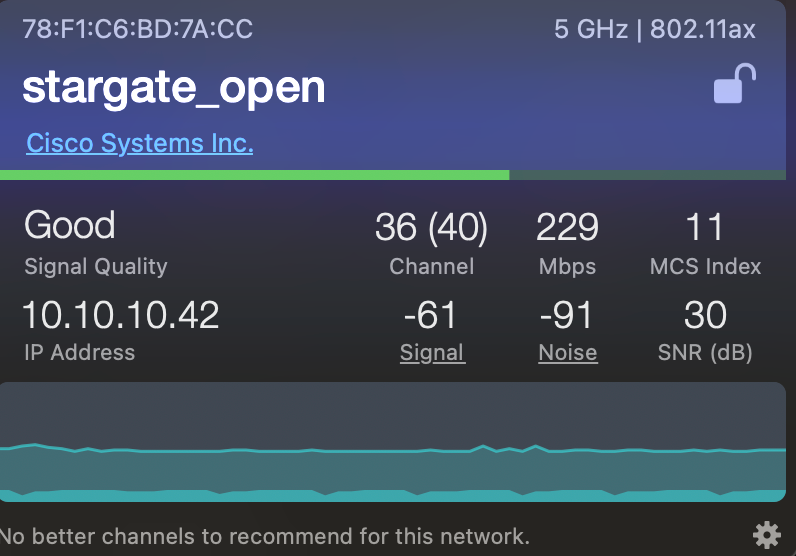
When the client support OWE it will contact the SSID stargate_open, but behind the scenes, it’s connected to the stargateOWE SSID. Here you can see I am connected to stargate_open, but my WiFi signal app shows stargateOWE

Note the lock infront of the stargateOWE and of not infront stargate_open, your traffic is encrypte. But there is no authentication verification, but it looks like in MacOS encryption is enough to show the lock.

If you not hide the OWE SSID (which is recommended) it will also show you connected to stargateOWE instead of stargate_open on your IOS device. Also, note here that it doesn’t show the lock :).

In any case, the Wi-Fi network only shows the stargate_open network from the client perspective., because normally you would hide the SSID and on vendors like Aruba this OWE is randomly generated by the SSID of the controller which can look very ugly. Technically WPA3 capable clients can directly connect to stargateOWE.
Also note that there is no lock next to SSID and showing Unsecured Network, that’s because the AP cannot verify who you are. But when connected with OWE your traffic is encrypted non OWE clients will not have their connection encrypted as you would connect with a normal Open network/SSID
Basically, when you disable the 2.4 GHz network on the stargateOWE WLAN, it will only allow clients that connect with 5 GHz. And the 2,4ghz client will just connect with the normal authentication open network.
Bonus:
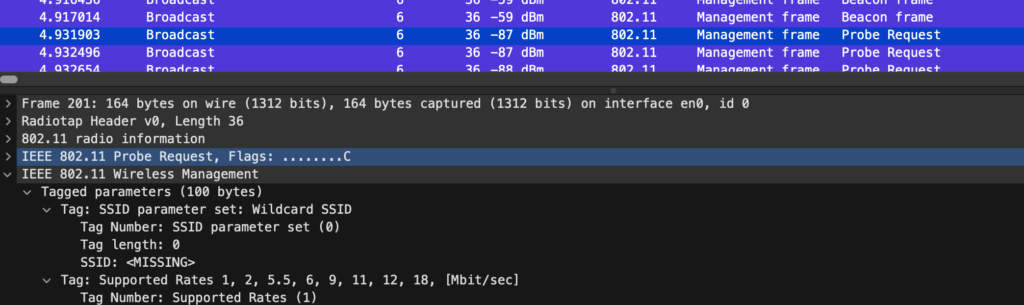
So what happens when you do not connect through the op SSID but try to connect directly to the stragateOWE SSID? I turned on broadcasting on the SSID but it’s not pickup by the client’s discovery process.
It is broadcasting
The Client asking for all SSID
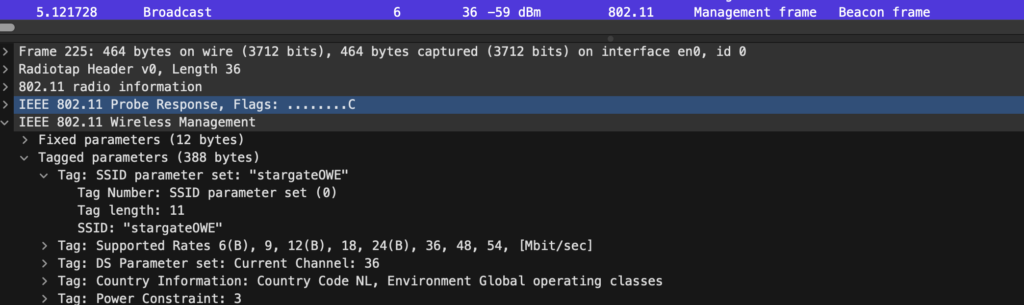
The AP responded with the “stargateOWE” SSID
But the client just doesn’t see it:
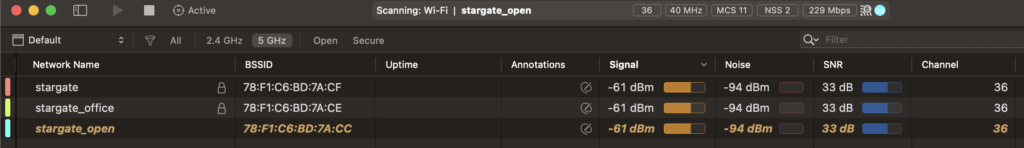
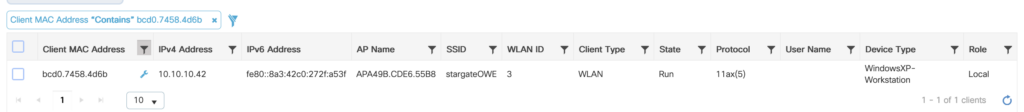
And the mechanism of OWE still works correctly as you can see clients join the stargateOWE said through the stargate_open SSID
On the client:
Security
Now the device traffic is encrypted but your network is free for everyone to join, joined client STA can’t eavesdrop but they can actually attack you, So make sure you configure peer-blocking on both WLAN’s. To prevent malicious users from attacking other clients.
