There is often alot of confusion between Hotspot 2.0 and passpoint, so let me get that out of the way first.
Hotspot 2.0 is a technology that enables seamless and secure roaming, while Passpoint is a certification program for Wi-Fi networks that are built on top of the Hotspot 2.0 technology, developed by the Wi-Fi Alliance for Wi-Fi networks that support the Hotspot 2.0 technology. Passpoint-certified Wi-Fi networks provide a seamless and secure roaming experience for users, while OpenRoaming aims to extend these benefits to a wider range of Wi-Fi networks through an underlying federated identity system.
Both the Hotspot 2.0 (Wi-Fi Alliance) and 802.11u (IEEE) tech specs spell out the mechanisms and protocols that will be used to enhance Wi-Fi. 802.11u/Hotspot 2.0 protocol enhancements will enable Wi-Fi to live up to the
next wave of business requirements being asked of it, especially as it relates to enhanced security, easier access, and more user-friendly operation.
With that said, let us continue building an OpenRoaming on a Cisco SDA-enabled network.
So how does a Wireless Client connect to a hotspot 2.0 network like OpenRoaming.
Clients can use active (probes) or passive (beacons) scanning techniques to discover APs
First, we have Passive discovery (beacons from AP) that the client hears.
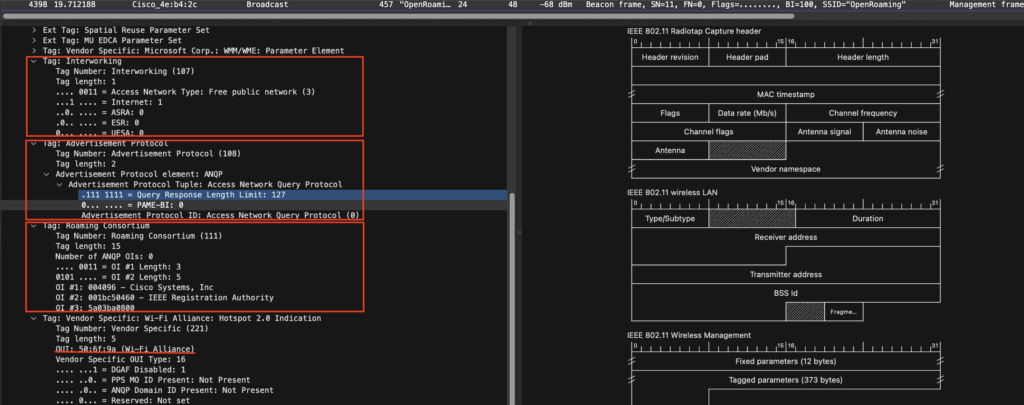
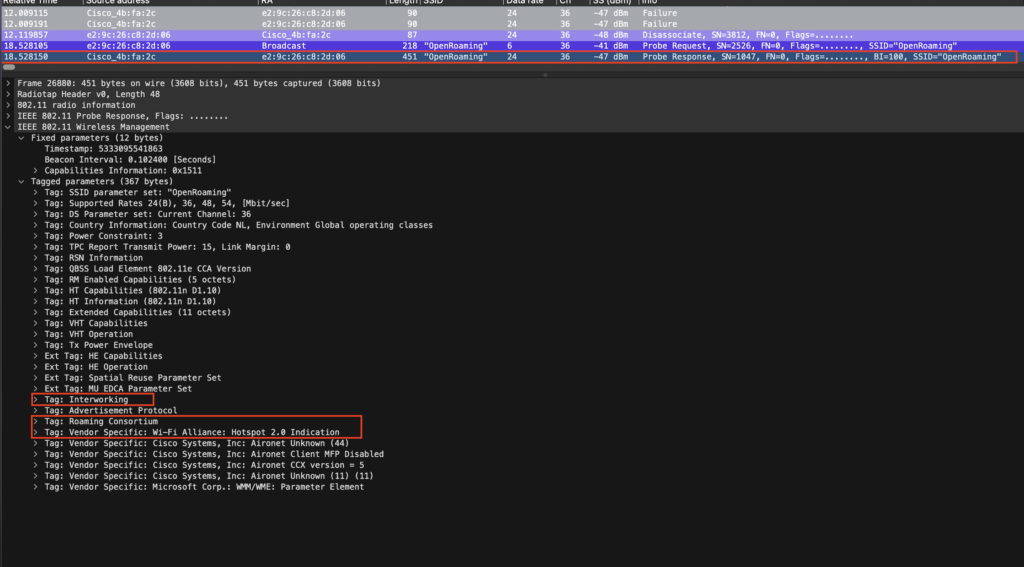
From top to bottom:
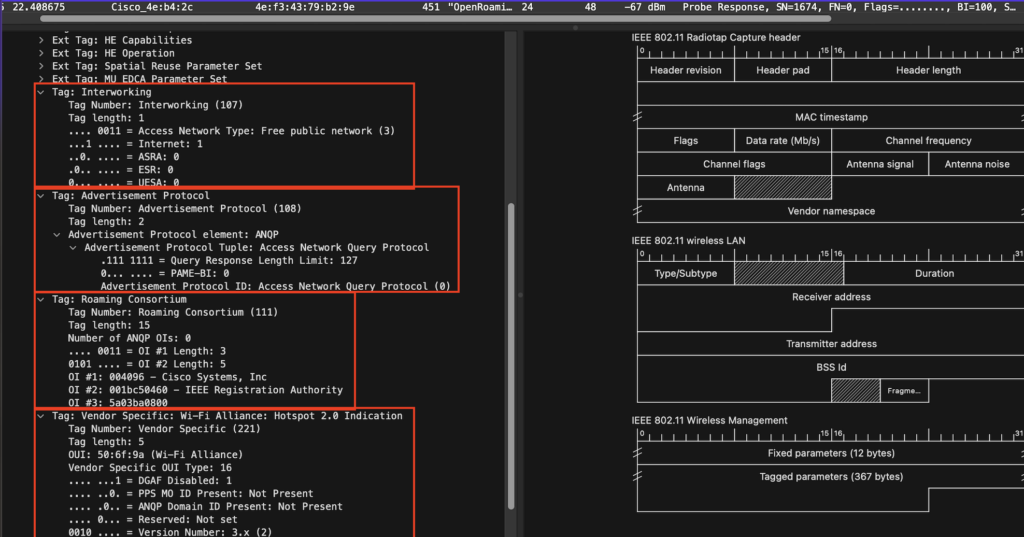
Interworking Element
Identifies the interworking service capabilities of the AP or client.
Is there internet access yes or not. It also tell what kind of network is it, this can be:
– Private – home and enterprise networks
– Private with guest access – enterprises offering guest connectivity
– Chargeable public network – available to anyone, but requires a fee
– Personal device network—for peripherals in an ad-hoc mode
– Free public network – available to anyone, no fees
– Emergency services only
We configured the network as a Free public network . You can that see it here in the configuration we used before:
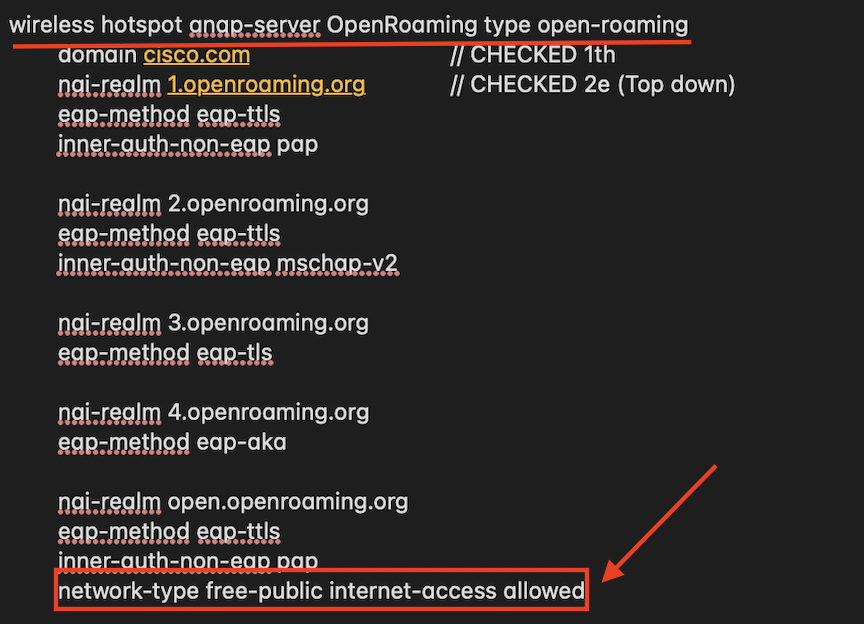
if it is a “Private with guest access – enterprises offering guest connectivity” is debatable.
ASRA set to 0
The interworking protocols are interested in solving problems with modern Hotspots, notably security problems. However, the ASRA information is for unsecured networks that are akin to today’s open public networks. The ASRA field tells the higher layer protocols on the client device what steps to take (e.g. URL redirection, terms and conditions, etc.) after the connection is made.)
ESR set to 0
The ESR element uses information such as the caller’s location and the type of emergency to determine the correct PSAP to route the call to
UESA
Unscheduled Emergency Services Association) flag to not
There is also a Venue info element when it is configured, but that’s not mandatory
Advertisement Protocol
Identifies the network’s support for particular advertisement protocols, such as ANQP, which allow the client to learn more about the network by querying the AP prior to forming a connection
Roaming Consortium
Identifies service providers or groups of roam- ing partners whose security credentials can be used to connect to a network.
Roaming consortiums are identified by an organization identifier (OI) that is assigned by the IEEE—similar to the first half of a MAC address. An OI is often 24 bits in length, but can also be 36 bits
(i.e. OUI-36). OIs are globally unique, identifying a manufacturer, operator, or other organization
During network discovery and selection, the client device
will receive this list of OIs and determine if any of them meet the device’s connection and roaming policies. The Roaming Consortium element can include up to 3 OIs in the beacon, but will also notify clients if additional OIs are available via ANQP query (e.g. “Number of ANQP OIs”).
Vendor Specific: Wi-Fi Alliance: Hotspot 2.0 Idication
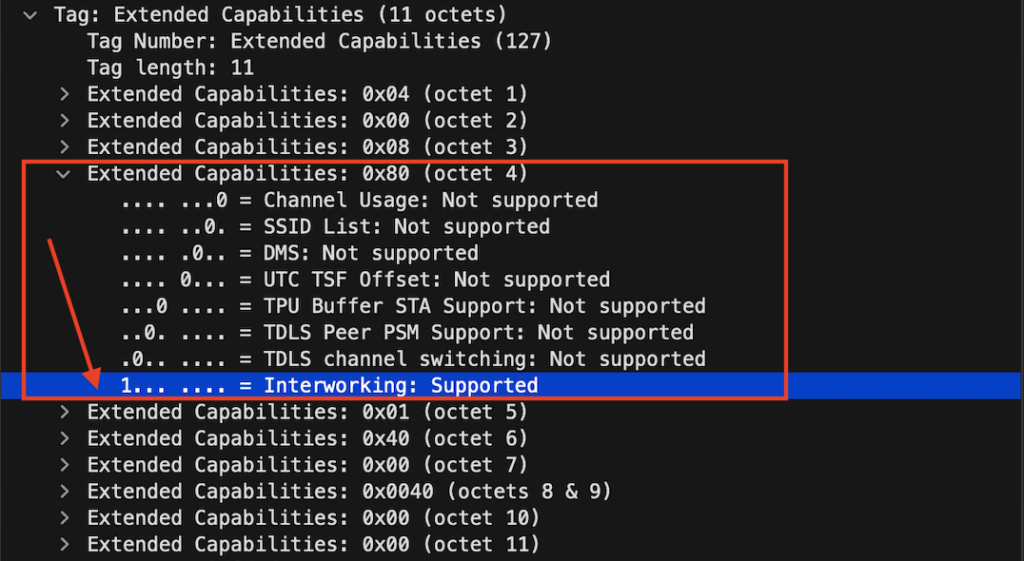
Indicates whether an AP supports 802.11u interworking features. It’s the replacement of the tag that we can see in the Extended Capabilities. The interworking is flagged to 1 to let clients know it’s a 2.0 hotspot network.
Here is a screen of the old variant which still will be included in the beacons
Extended Capabilities Advertisement Protocol :
Active scanning (Probe response) sent by AP with SSID unique to AP with information for HS 2.0, which AP sent in beacon frames. Same as information in the beacons (passive scan).
After the above discovery mechanism is done the client can decide to Join the OpenRoaming SSID by sending an action GAS frame Query.

A Gas Query is a so-called Public Action frame initiated by the client before an association is formed. The purpose of the GAS query is to discover and connect to a wireless network. It is part of the 802.11u standard, which defines the methods for accessing additional information about available wireless networks. The Gas Query is used by a client device, such as a smartphone or laptop, to query an Access Point (AP) for information about available networks.
ANQP information is carried within GAS Action frames. Specifically, the GAS frames include ANQP elements. The client sends a GAS Request, providing a list of ANQP elements that it wants to receive from the AP. The AP either satisfies the query out of its own configured datastore or relays the client’s query to backend advertisement servers. The backend encapsulation protocols are not specified by 802.11u or Hotspot 2.0.
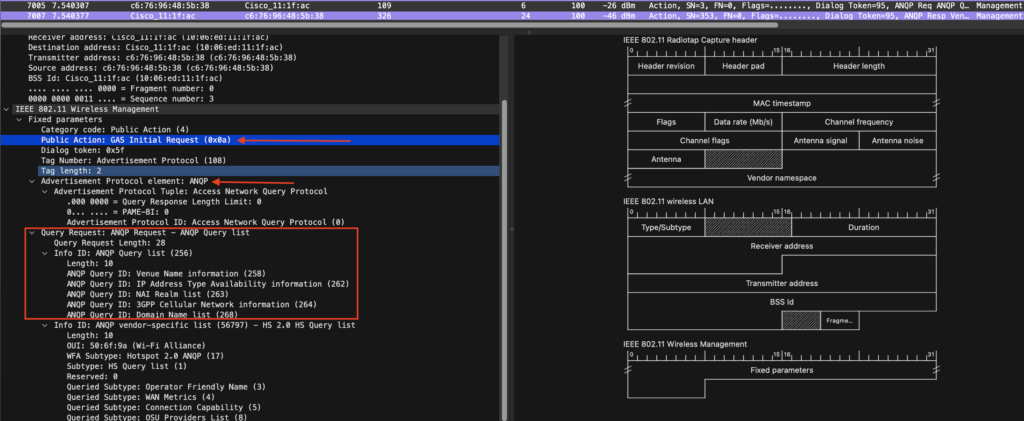
The AP will then With a GAS response which includes the ANQP elements requested by the client. The AP will respond with a GAS Advertisement frame, which includes information about available networks, containing NAI realm, domain, and authentication method. Together with some vendor-specific ANQP elements that can be used for a smoother handoff between Wireless and Cellular. The client device can then use this information to select the appropriate network and establish a connection.

NAIRealmlist
The NAIRealmlist is a component of the Hotspot 2.0 specifications. Hotspot 2.0 is a standard for secure, seamless, and automatic Wi-Fi connectivity. NAIRealmlist is a list of network access identification (NAI) realms that are supported by a given access point (AP). An NAI realm list provides a way for client devices to discover the available realms and the authentication method used by each realm.
The NAIRealmlist is included in the initial management frames that a client device receives when it scans for available Wi-Fi networks. This list allows the client device to make an informed decision about which network to connect to, based on its own capabilities, the available security methods, and the desired level of security. By supporting the NAIRealmlist, Hotspot 2.0 enables clients to easily and securely connect to Wi-Fi networks with minimal user intervention.
The NAI Realm list can also optionally indicate the Extensible Authentication Protocol (EAP) types supported by each realm as well as the authentication parameters for that EAP type. This is interesting for example if you want eduroam users to connect with their credentials to an OpenRoaming network.
DomainNamelist
lists one or more domain names for the entity operating the AP. This is critical for Hotspot 2.0 network selection policy, as it identifies the operator of the network. It indicates to the mobile device whether they are at a home or visiting Hotspot, I configure Cisco for now but will later change in when it is in production.
The association request is initiated by the client, followed by an association response, and open auth, and then the client will start an EAP-TTLS authentication handshake.
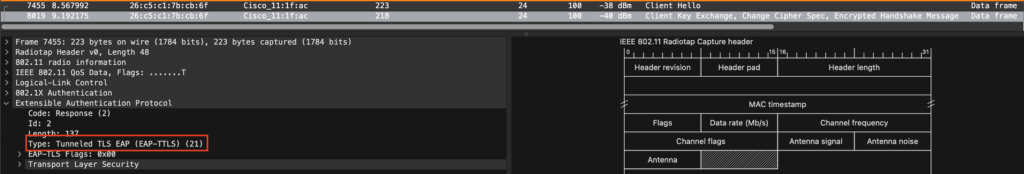
Upon success, followed by a complete 4-way handshake
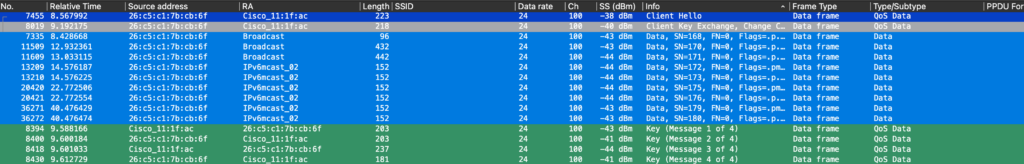
GAS is not always seen, for example with an iPhone 11 and the Cisco openroaming APP we see no GAS public action frames, however we see the information needed in the probe response frame.
Below is a screen of the full onboarding of an iPhone 11
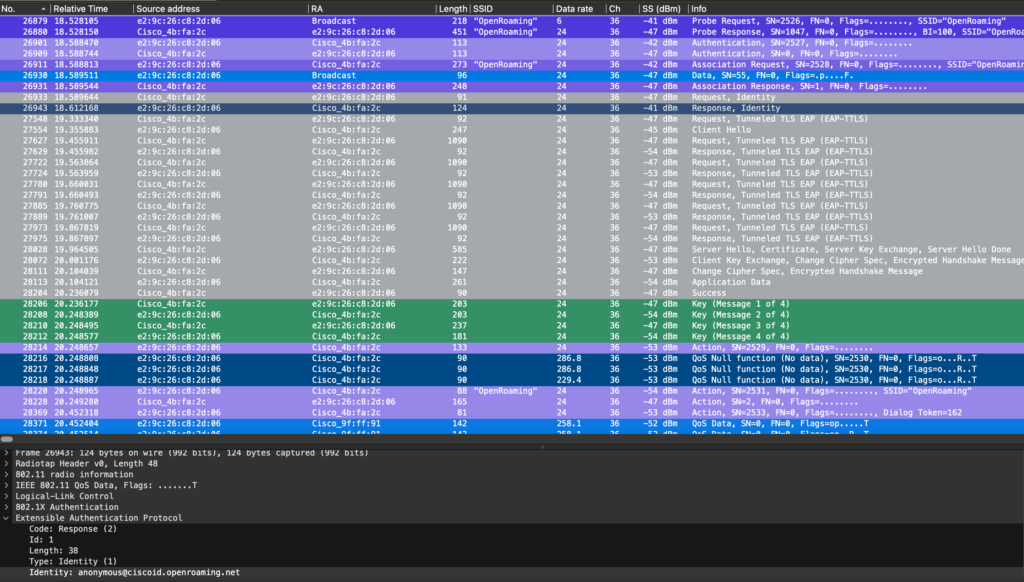
anonymous@ciscoid.openroaming.net we see in the outer message this is a dummy username. But we will see this also in the real identity response message inside the encrypted tunnel.
Hey Andy, I am trying to understand if there is no cellular handoff then is it normal 802.1x authentication? Trying to understand the use cases and reason why one should go for OpenRoaming.
Correct, 802.1x is a standard that uses EAP methods to connect. For instance, it is possible to authenticate a provider’s sim using 3G(EAP-SIM) 4G(EAP-AKA).
The use case concerning OpenRoaming is similar to Cellular Roaming, which provides access by having roaming agreements with other Hotspot operators (partners) OpenRoaming partners with Samsung and Google, imagine what they can do when partnering with IOT vendors. In this way, your device is already provisioned for access to an OpenRoaming-enabled network. By advertising 802.11u info, phones can make a good decision if they want to auto-connect or not.