When configuring OpenRoaming in an SDA fabric enable wireless environment it’s not seamless (yet).
The problem is that the configuration pushed to the WLC from DNAC (Version 2.3.3.6-70045) is limited and building an SSID with the unique fabric tags and unique. The solution is that we need to use a little bit of both, automated and manual configuration. There is no guide for this build so I’m going to explain the build in this blog article. To follow this guide, a basic setup of the fabric network needs to be in place already.
Step 1: Create a profile in Cisco Spaces
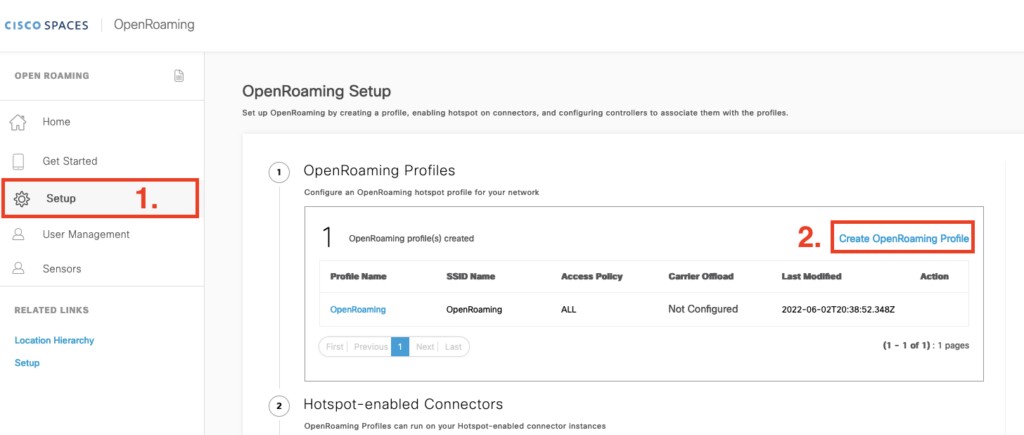
We want to accept all guests, we don’t want FT enabled because we can use adaptive to support Apple and late android devices. But for this test, we want to have a brought client compatibility as much as possible.
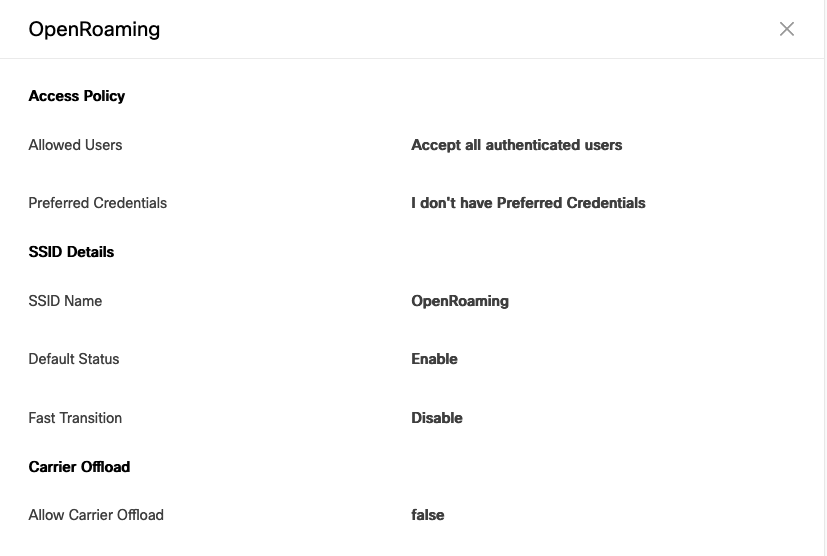
The profile part is now done.
Step 2: the connectors are already configured to communicate with the WLC and back to Cisco Spaces. If you didn’t set this up yet you can follow Cisco’s guide.
Note: make sure you enable the Hotspot-enable feature in the Spaces Connector(s).
It’s possible to Setup in a High Availability way like I did. In this way, a guest gets still gets authenticated when one connector goes down.
Step 3: shows the controllers that are connected with the DNASpaces connector VMs, We select the controller and
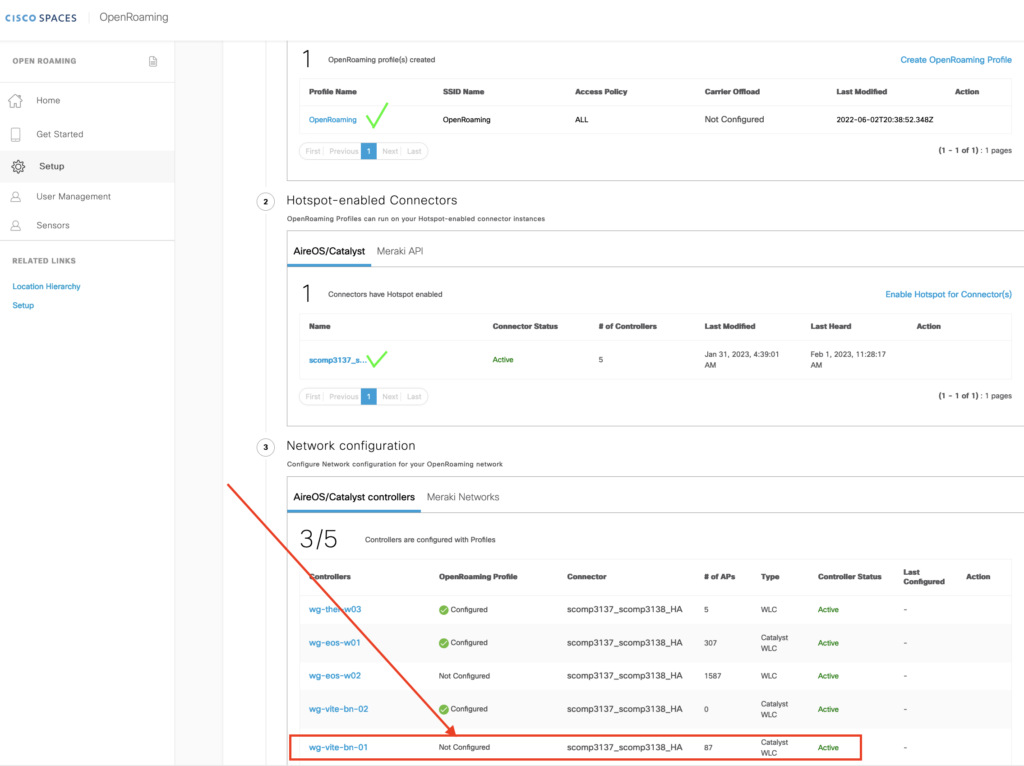
Select the controller name where we want to apply the profile we just created to
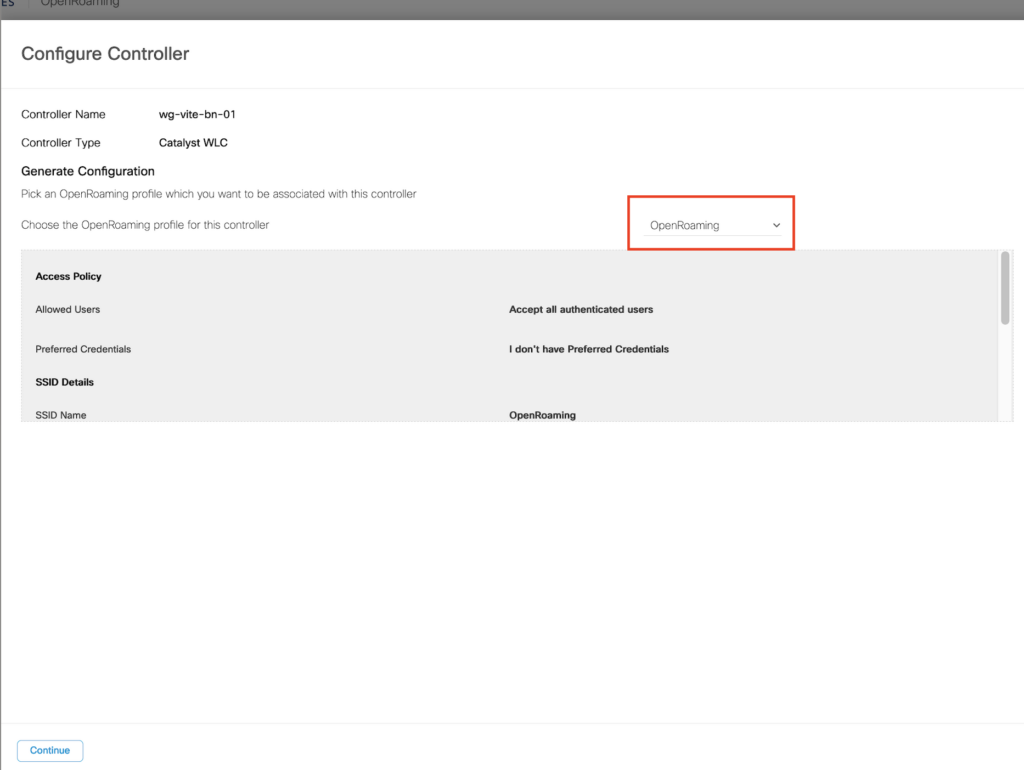
Select Continue and fill in the Wlan Name (Use the same name as we created in DNAC before, it will help to build a preconfigured example output)
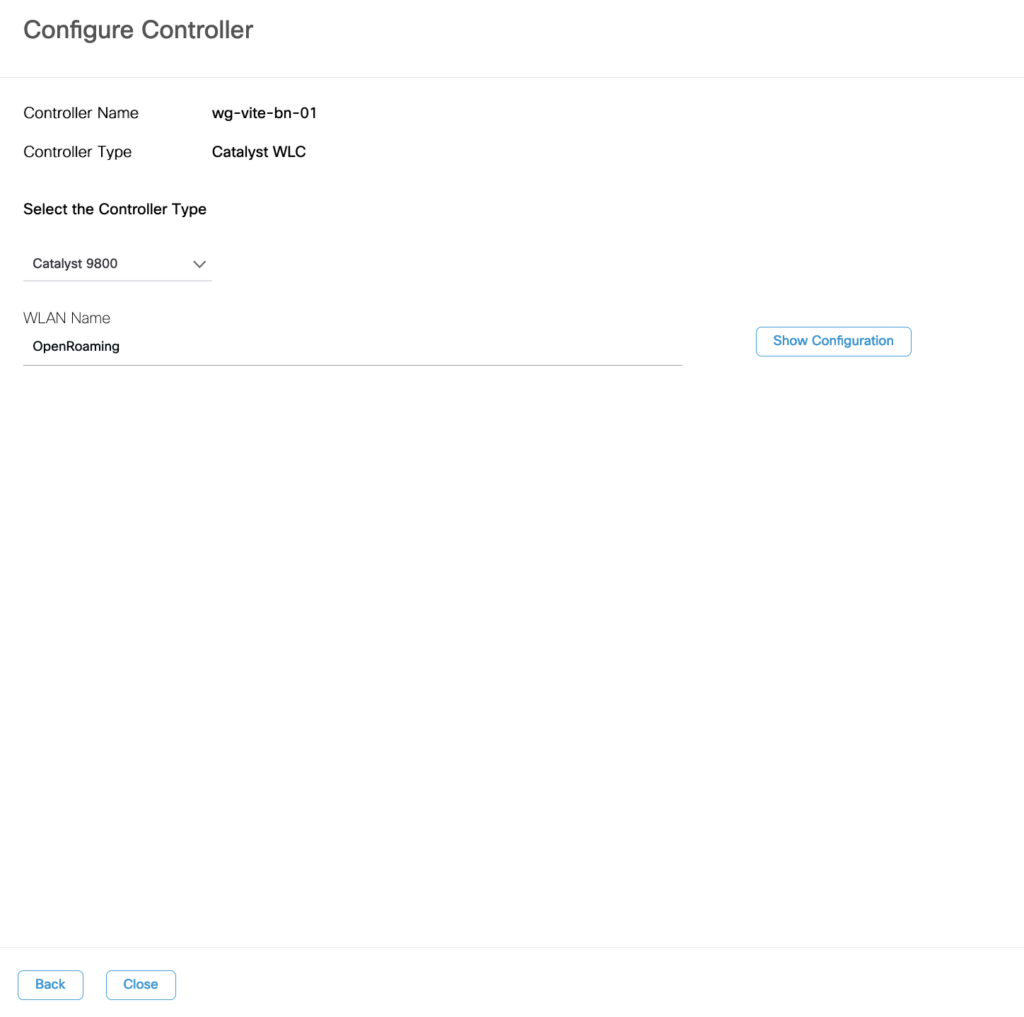
Now we got an example config, but this will not apply for SDA Fabric WLCs, so we need to change this example config to work with the Fabric-enabled WLC.
In DNAC we first create an SSID with the name OpenRoaming, and align the amendments with the profile config in Spaces. Then we log in to the WLC and find the unique created Wlan profile by DNAC.
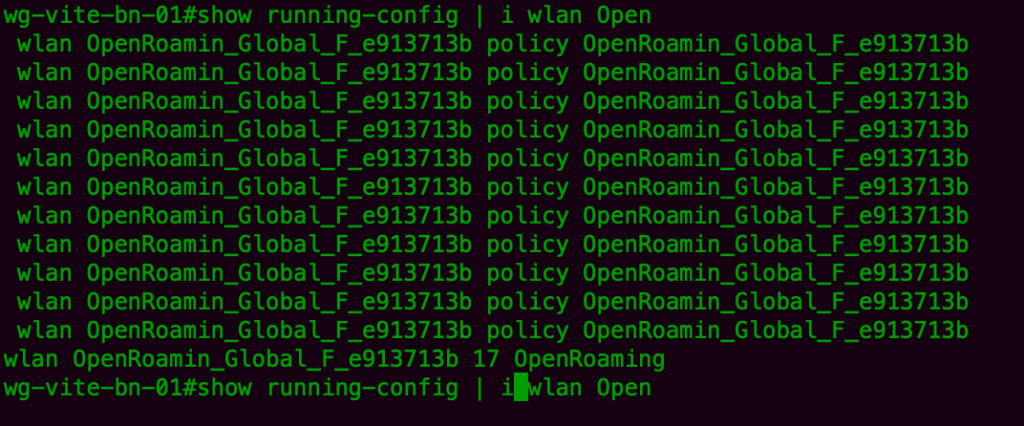
We add the authentication list “security dot1x authentication-list OpenRoaming_wg-vite-bn-02_AUTHElist and remove the de default authentication list that was generated by DNAC.
wlan OpenRoamin_Global_F_e913713b 17 OpenRoaming
shut
!!! No security dot1x authentication-list default
!!!! security dot1x authentication-list OpenRoaming_wg-vite-bn-02_AUTHEList
no shut
Add the domain, realm and OI information
wireless hotspot anqp-server OpenRoaming type open-roaming
domain cisco.com // CHECKED 1th
nai-realm 1.openroaming.org // CHECKED 2e (Top down)
eap-method eap-ttls
inner-auth-non-eap pap
nai-relam 2.openroaming.org
eapa-method eap-ttls
inner-auth-non-eap mschapv2
nai-realm 3.openroaming.org
eap-method eap-tls
nai-realm 4.openroaming.org
eap-method eap-aka
nai-realm open.openroaming.org
eap-method eap-ttls
inner-auth-non-eap pap
network-type free-public internet-access allowed
open-roaming-oi All beacon. // CHECKED 3th. NOTE: Only 3 Roaming OI can be advertised as Beacon
roaming-oi 001bc50460 beacon / eduroam
roaming-oi 5a03ba0800 beacon // .edu
If the beacon keyword is specified, the roaming OUI is advertised in the AP
WLAN beacon or probe response. Otherwise, it will only be returned while performing the roaming OUI ANQP query.
Add the radius server ( pointing to the Spaces Connector)
radius server OpenRoaming_scomp3137
address ipv4 10.x.y.51 auth-port 1812 acct-port 1813
key radsec // key is public available
radius server OpenRoaming_scomp3138
address ipv4 10.x.y.52 auth-port 1812 acct-port 1813
key radsec // key is public available
The Group that contain the radius servers
aaa group server radius ORSG
server name OpenRoaming_ServerNameX
server name OpenRoaming_ServerNameY
mac-delimiter hyphen
Globaly bind the list with the group
aaa authentication dot1x OpenRoaming_wg-vite-bn-02_AUTHEList group ORSG
aaa authorization exec OpenRoaming_wg-vite-bn-02_AUTHZList group ORSG
aaa accounting identity OpenRoaming_wg-vite-bn-02_ACCTList start-stop group ORSG
radius-server attribute wireless accounting call-station-id ap-macaddress-ssid
radius-server attribute wireless authentication call-station-id ap-macaddress-ssid
!! wireless profile policy OpenRoamin_Global_F_e913713b
shut
Hotspot anqp-server OpenRoaming
accounting-list OpenRoaming_wg-vite-bn-02_ACCTList
no shut
Note: Disabelng the policy profile will result in associated AP/Clients to rejoin.
wireless tag policy default-policy-tag
description “default policy-tag”
!! wlan OpenRoaming policy default-policy-profile << is already added during SSID added on the fabric
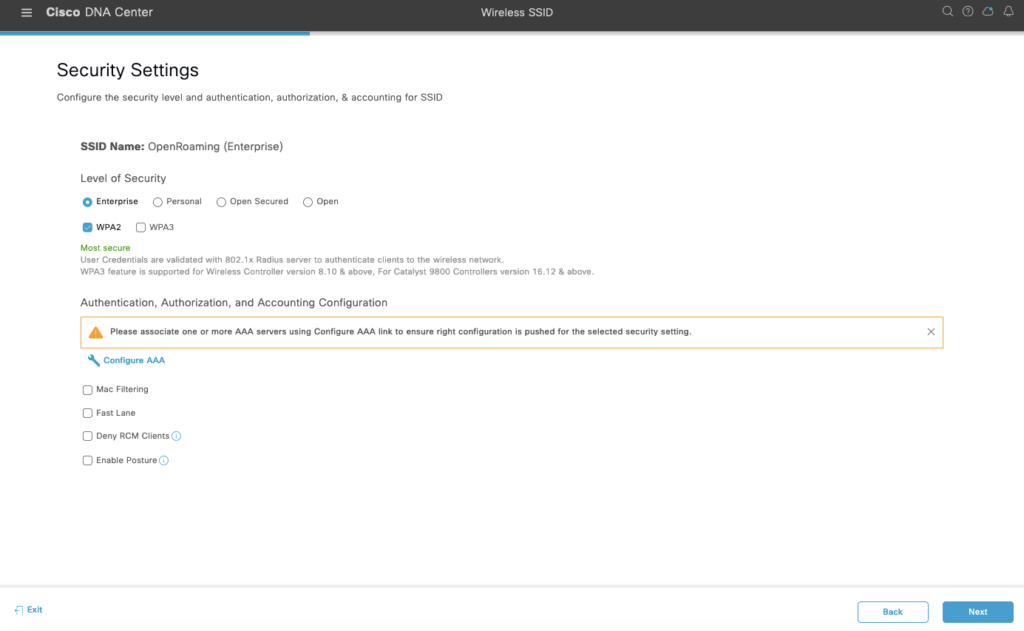
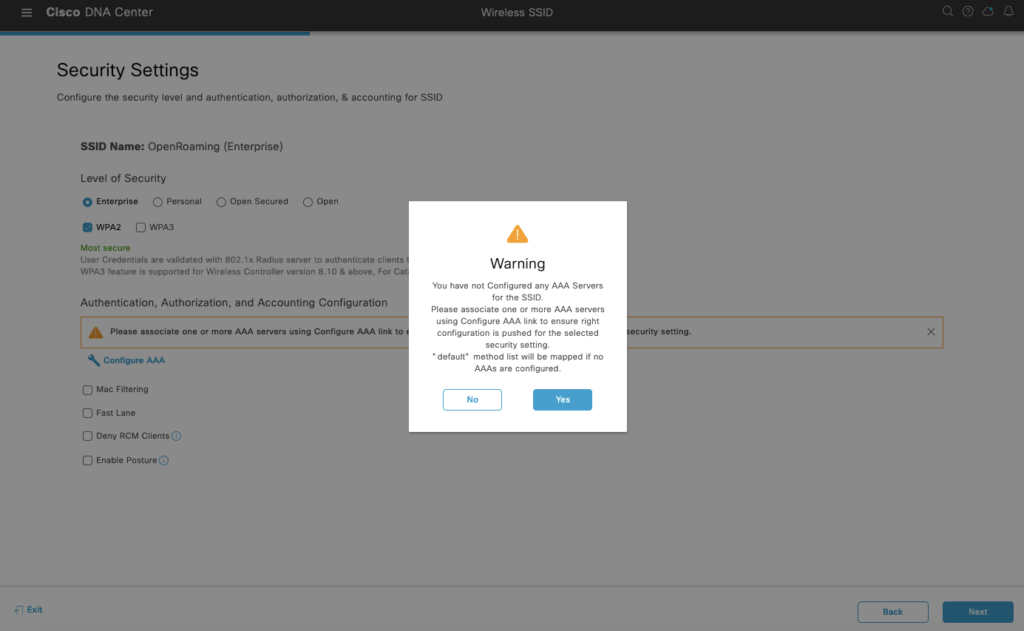
We want to bring compatibility at first so we disable 802.11r and 802.11v which can cause association problems. Later we tune this.
802.11k will not cause client compatibilities issues, it’s a suggestion that the AP gives the client, and if the client doesn’t want to do anything with it or cannot read the information element it will be ignored by the client.
We want to have the AP Site Tag included, so we can later build more granular policies based on the Building where it is coming from.

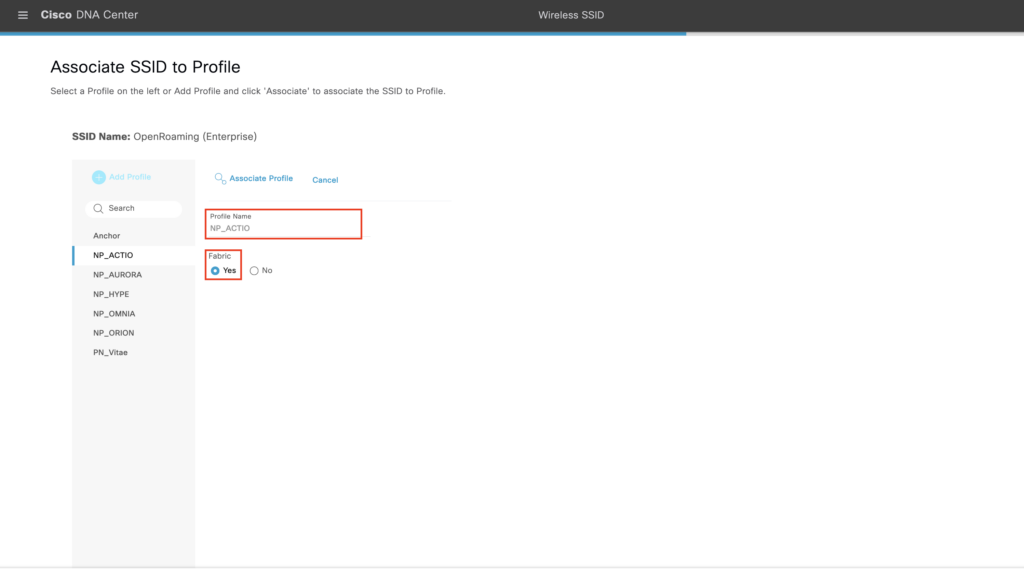
Select Associate Profile
PROVISION THE WLC
Then we provision the WLC to make the SSID available at 2 sites, during the summary you can see what is provisioned.
The below Fabric Config is pushed toward the WLC that is provisioned. It will remain disabled even when we say configure it for admin enable.
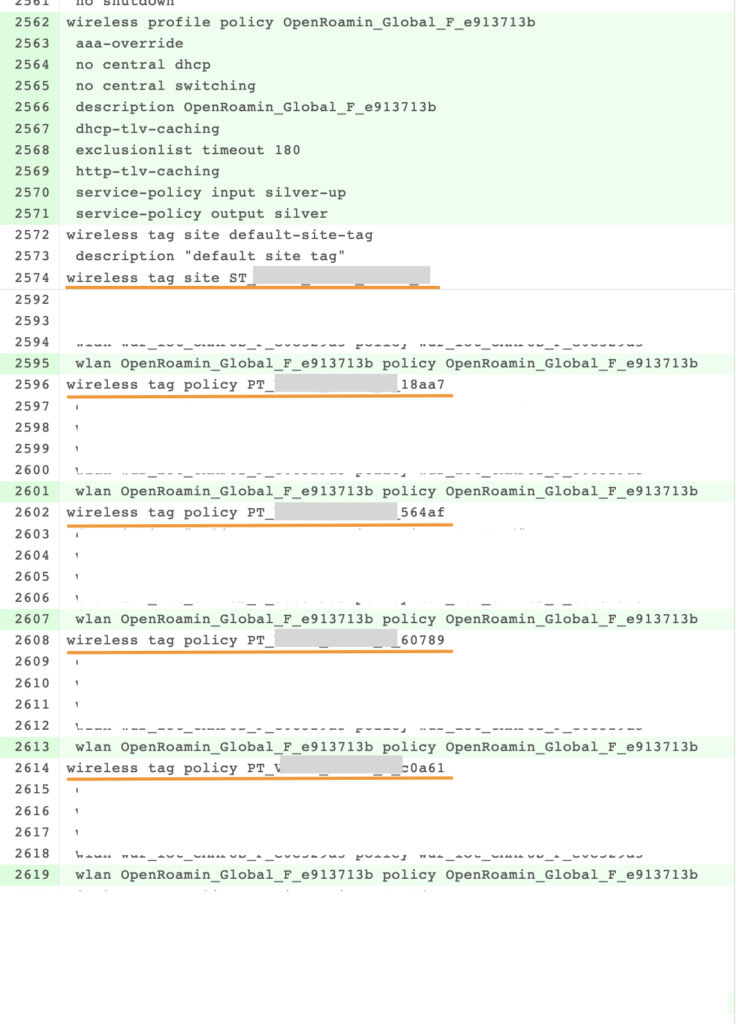
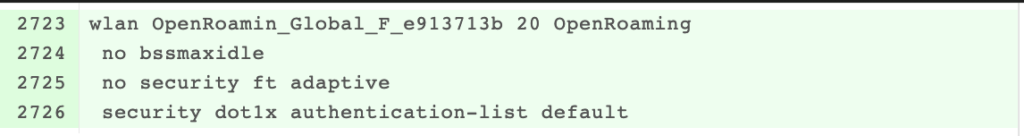
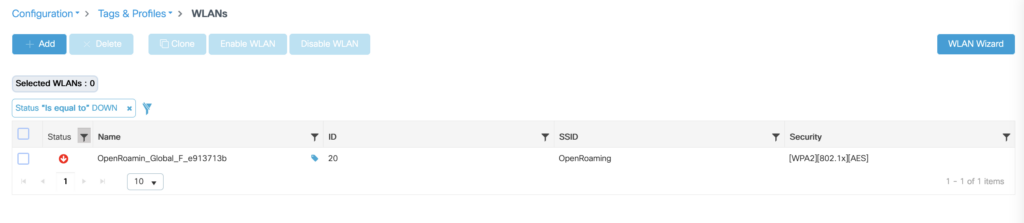
At this point, the config is applied to the WLC, but because it is a fabric enables the WLAN will stay down till we attach a network to it.

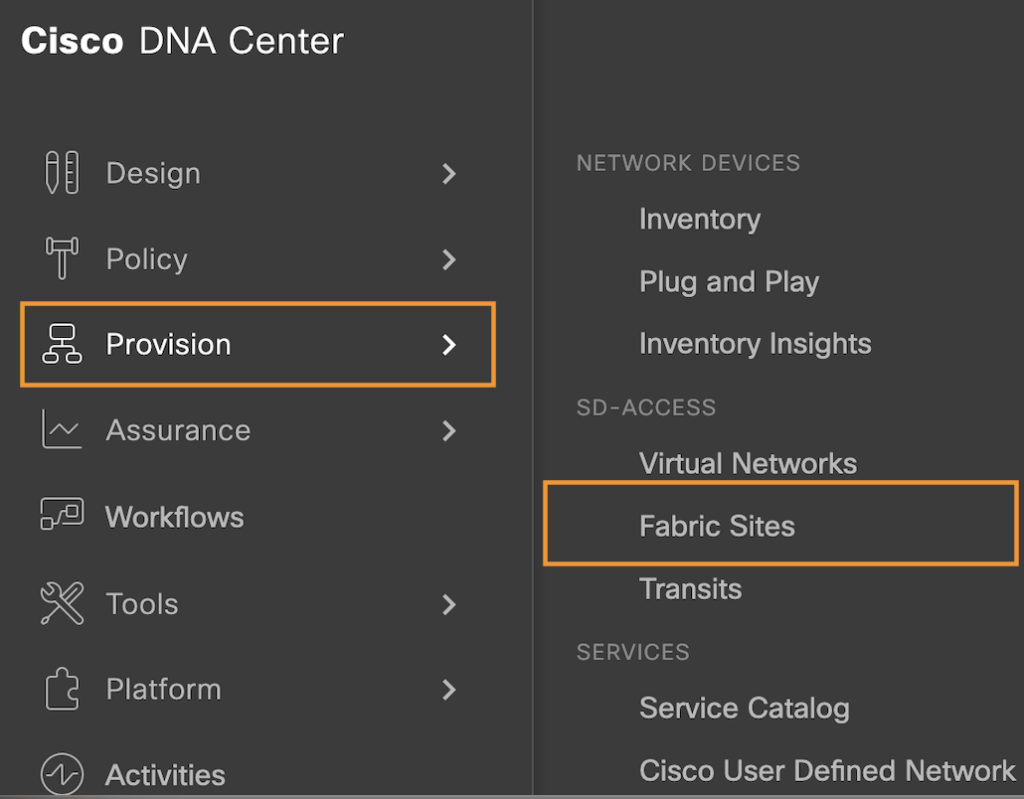

Select the Fabric site and go to the “Host Onboarding Tab” under Wireless SSID to Assign the address Pool.
The SGT we don’t need to fill in because ISE will take care of it during the client STA onboarding.
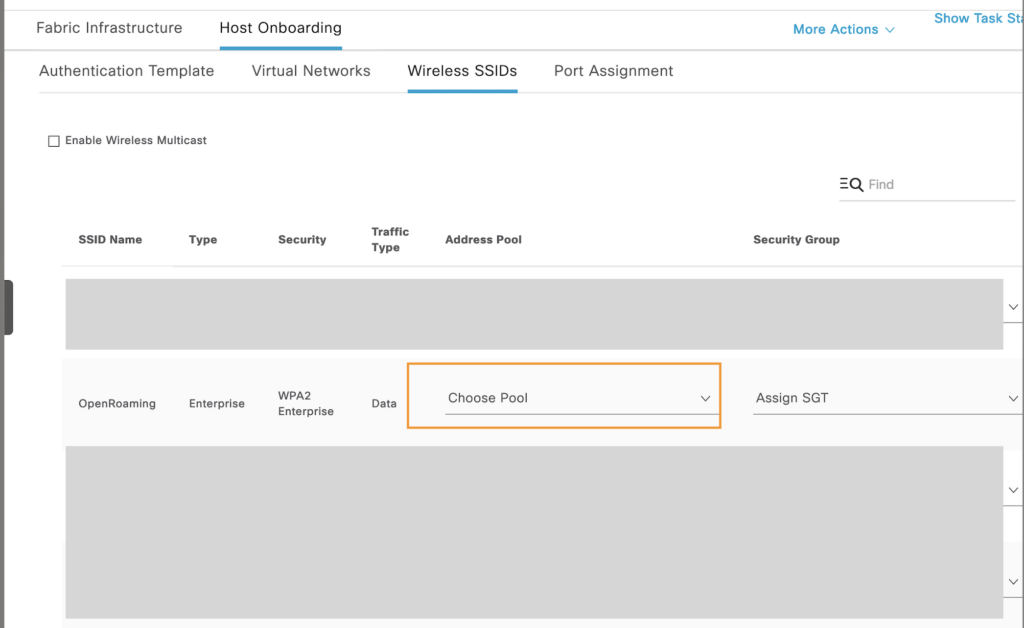

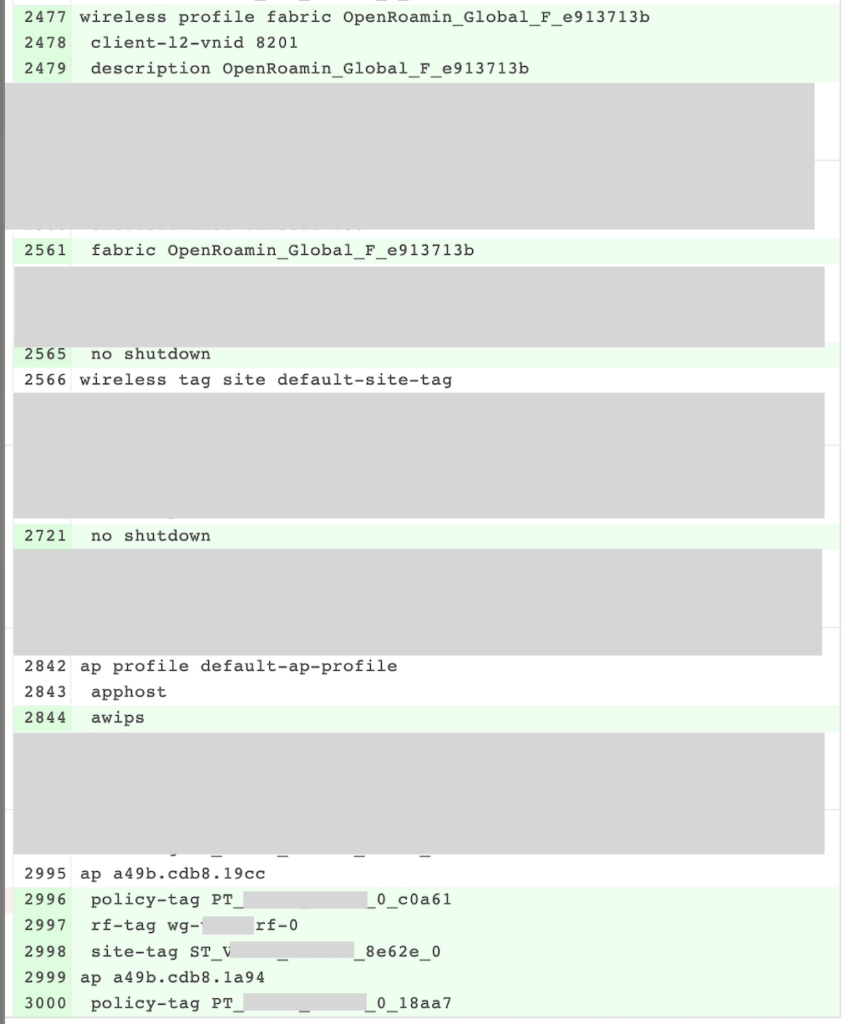
Hit apply, and this is will configure the Fabric Border and Control Plane border with the following configuration. Also, the Policy tag will change again because this Fabric Border runs the eWLC
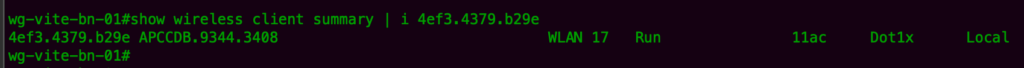
Connect a client
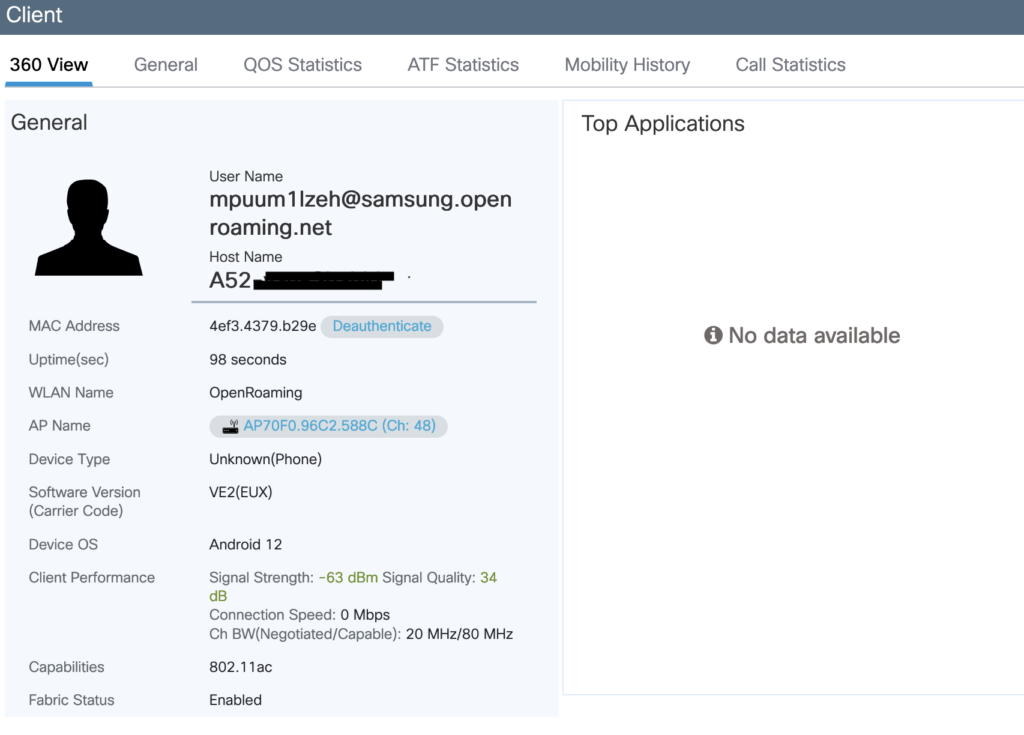
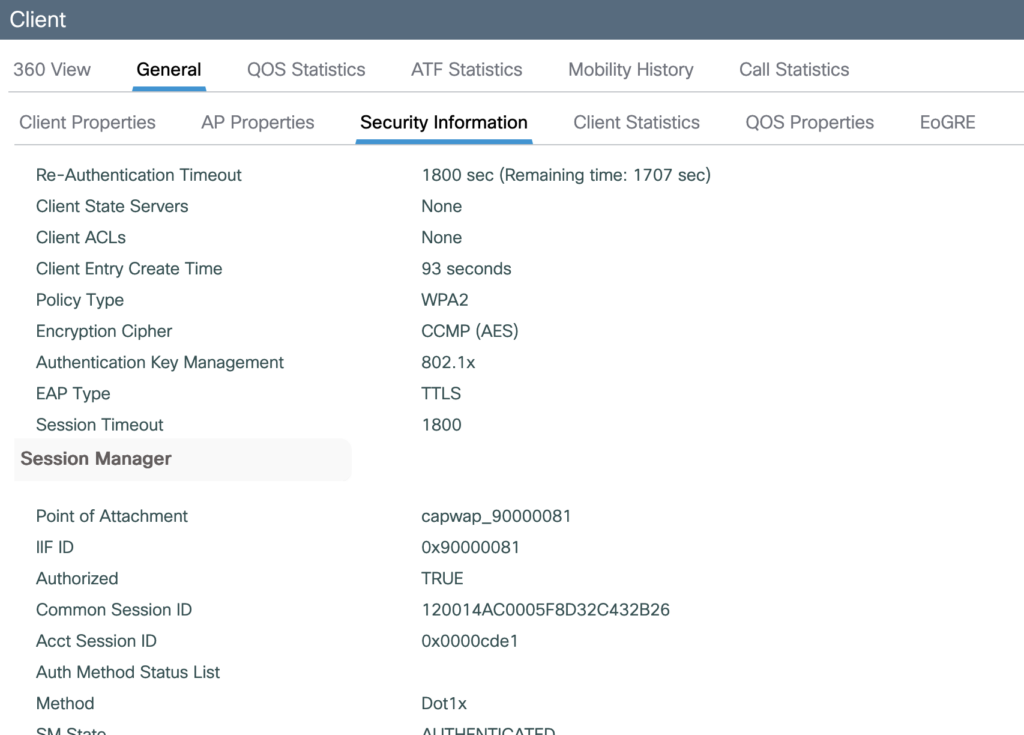
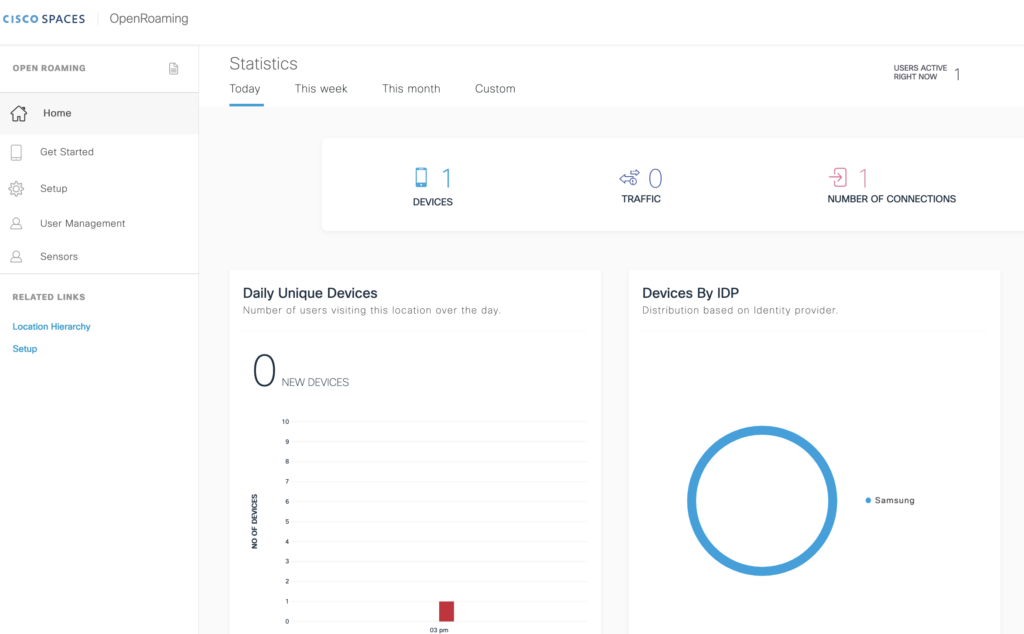
This is all that we can see in Cisco Spaces when a client is connected.